Table of Contents
LDAP authorization function
The description is valid for software version 2.10.119.99 and newer.
. Activating the authorisation function via LDAP does not disable the inbuilt accounts, but supplements this mechanism. To use local accounts, select Authentication=Internal User in the Storage settings of the client application and continue to use the accounts created in the Storage module.
In the 2.10.37.99 version, the ability to authorise media storage users via the LDAP protocol has been added.
General Information
- LDAP (Lightweight Directory Access Protocol) is an open standardised protocol used for various directory service implementations, including Active Directory. LDAP allows users to access resources based on the permissions configured by the directory service administrator.
- Active Directory (AD) is a proprietary implementation of Microsoft's directory service - a set of software services and databases for hierarchical representation of company resources (departments, computers, printers, network drives, etc.) and configuring access to them.
How It Works
- In the module Storage (
Administrator Control Panel→Status→Storage_N→Manage Users…→Manage Groups→Add New Group) user groups are created that will correspond to the implemented technical process (for example: Skylark Editors, Skylark Operators, Skylark Users, etc.). - In the Directory Service, user groups are created with the same names as defined in the Storage module. If you are using Active Directory, this can be done through the Active Directory Users and Computers snap-in
dsa.msc. - Users are only created in the Directory Service.
- Users created in the directory service are assigned the desired groups based on their role in the workflow.
- If authentication is successful, all groups assigned to the user will be retrieved from the memberOf attribute.
- The retrieved groups will be matched with the groups created in the Storage module, if a match is found, then rights of such group are assigned to the user. The built-in Everyone group is assigned to the user in any case.
In addition, user name, phone number and email address information can be downloaded from the directory service and synchronised on a regular basis.
When a user is authorised via LDAP, the login is cached for 30 seconds. This must be taken into account when working in a real system. For example, if a new group is assigned to a user in the directory service, its mapping may occur with the specified delay.
Obtaining Data from Active Directory
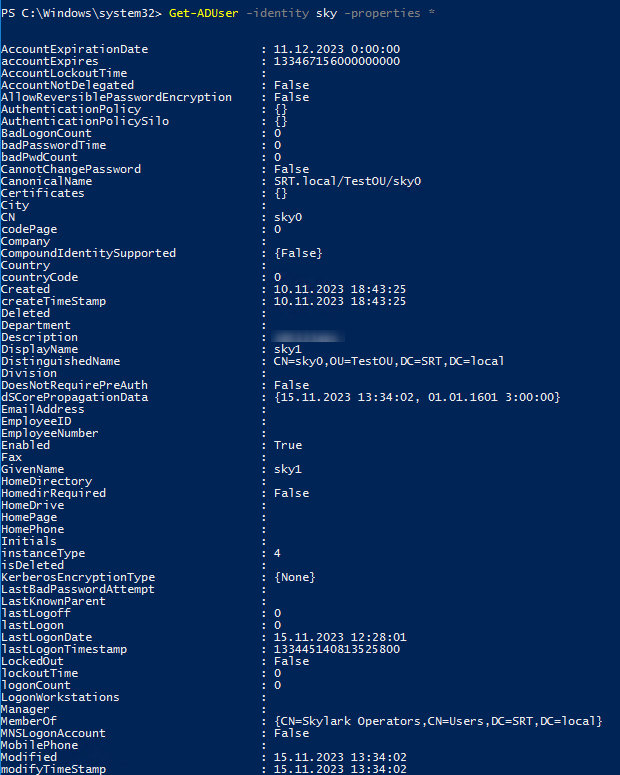
You can obtain the data required to configure the function using the Get-ADUser command in the Power Shell. You must run Power Shell as an administrator to display all available data.
Command examples:
Display a summary of user information:
Get-ADUser -filter *
Output extended information about the selected user:
GetADuser -identify <USERNAME> -properties *
A short list of frequently used values:
- DistinguishedName - the entry's location in the directory,
- MemberOf - list of groups associated with the user,
- SamAccountName - user login (e.g. sky),
- CN - user's display container name (e.g. sky),
- DisplayName - user's visible name (e.g., “User Skylark”),
- telephoneNumber - phone number,
- mail - email,
- ObjectClass - specifies the object type (e.g. user - user).
Configuration
Server Part
LDAP server connection parameters are configured on the tab: Administrator Control Panel→Manage→Storages→Storage_N→LDAP.
Client Side
To start using LDAP accounts, on the Storage| tab of client applications, select Authentication=LDAP and specify your directory service account details.
If the connection is successful, the media storage will switch to the online status and you will see the folders and files:
Application
The function can be used as part of MAM servers in large companies with centralised user account management based on directory services.